
The cryptocurrency landscape has reached a new level of threat with the emergence of a large-scale campaign dubbed “GreedyBear” by experts at Koi Security. Reported on August 8, 2025, the attack has already resulted in the theft of over $1 million in cryptocurrencies. The attackers used a combination of fake browser extensions, malware, and phishing websites.
This sophisticated operation highlights the evolving nature of cybercrime and poses serious challenges to users and the wider blockchain ecosystem.
Details of the GreedyBear Campaign
Researchers at Koi Security revealed that the GreedyBear group employs a multi-pronged strategy, combining counterfeit wallets—such as clones of the popular Exodus Wallet—with phishing websites and advanced malware.
Tuval Admoni, a cybersecurity expert at Koi, noted:
“Most groups pick one method—extensions, ransomware, or phishing. GreedyBear chose to combine them all, achieving remarkable success.”
A standout feature of this campaign is the use of AI-generated code, allowing the attackers to scale rapidly and adjust to new targets. The malicious tools are often disguised as legitimate applications, successfully passing initial security checks in browser extension stores before injecting harmful code into trusted platforms.
This points to a growing need for stricter oversight by browser developers and greater user awareness.
Related Threats and Trends
The GreedyBear operation is not an isolated event. In July 2025, Koi Security also reported a similar attack known as the “Foxy Wallet” campaign, involving over 40 malicious Firefox extensions believed to be created by Russian-speaking actors. These tools were used to steal wallet data through deceptive interfaces and background automation.
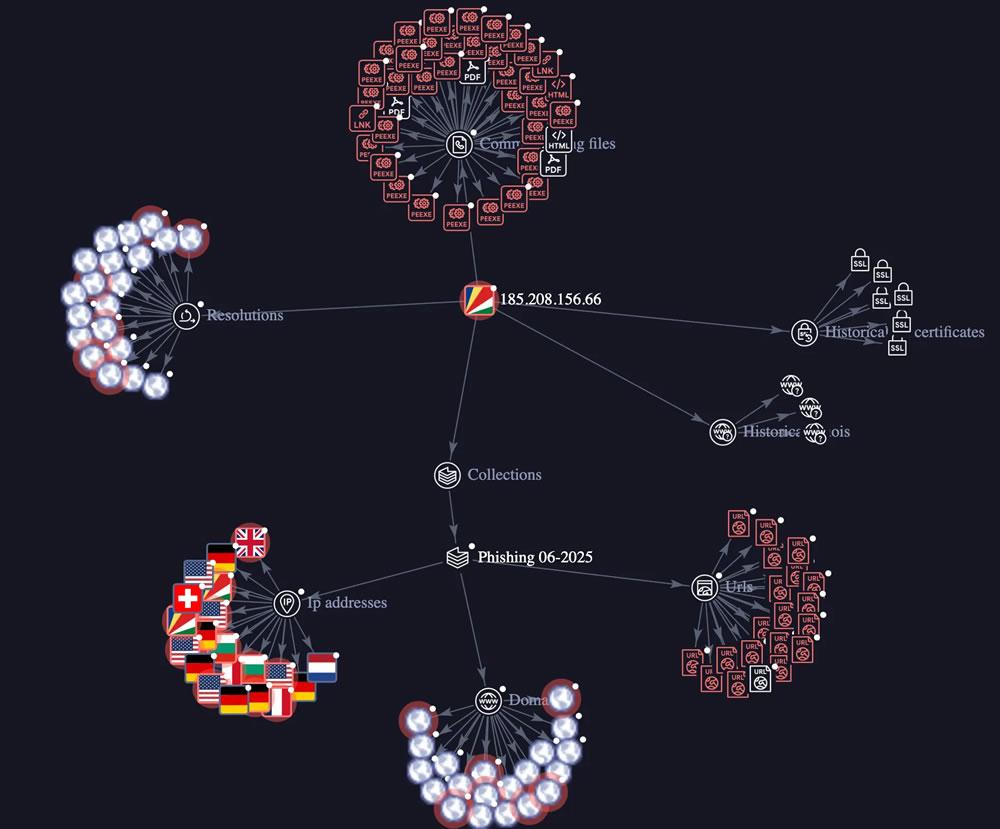
Other similar incidents include the theft of 256 ETH via malicious code embedded in YouTube videos, as documented by SentinelLABS. In all cases, attackers relied heavily on social engineering and AI tools to craft convincing schemes.
According to Chainalysis, crypto thefts totaled $2.2 billion in 2024, with 61% linked to North Korean groups like Lazarus. These actors have adopted complex strategies, such as fake job interviews and key compromises, to gain access to assets.
Implications for Users and the Industry
The GreedyBear case highlights the urgent need for improved security measures across the crypto sector. Cybercriminals exploit trust in browser extensions, websites, and social platforms, making user education more important than ever.
Best practices for users include:
-
Install extensions only from verified sources
-
Use hardware wallets for asset storage
-
Limit hot wallet exposure to the internet
-
Avoid clicking on suspicious ads or links, even from search engines
Beyond user behavior, the campaign may also affect market confidence, potentially encouraging tighter regulation of crypto-related tools and services. The shift toward more transparent and security-oriented standards could reshape how businesses operate and how users interact with decentralized systems.
Future Outlook and Recommendations
Experts warn that attacks like GreedyBear could become routine without comprehensive action. Key recommendations include:
-
Browser developers should implement stricter extension review processes
-
Crypto platforms must invest in threat detection systems
-
The industry should collaborate with cybersecurity firms
-
Regulators need to adapt quickly to new threat vectors
This latest campaign underlines the fragile balance between blockchain innovation and user protection. As technologies evolve, the crypto industry must remain proactive, adopting smarter defenses and continuously educating its user base.
Safeguarding the future of decentralized finance starts with recognizing that security is not optional—it’s essential. Be careful when working with cryptocurrency. And when working online in general. Learn how to protect yourself in Revbit’s guide, “What Happens If You Send Crypto to the Wrong Address.”